Every LINUX Command You Need In 15 Minutes
Every Hacking Command Explained As FAST As Possible
Want to master hacking commands in record time? In this video, we’ll dive into the essential tools and commands every ethical hacker needs to know—explained clearly, concisely, and at lightning speed. From file management and text processing to network exploration and system control, we’ve got you covered. Whether you’re just starting or honing your skills, this video is your ultimate guide to hacking like a pro.
📥 Get the Hacking Cheat Sheet Here: https://bit.ly/Pro-Hacking-Cheatsheet
💡 Disclaimer: This video is for educational purposes only. Only use these skills on systems you own or have explicit permission to test. Hacking unauthorized systems is illegal and unethical. Always practice responsible and legal hacking!
Here’s the full list of commands mentioned in the video:
System Navigation and File Management Commands
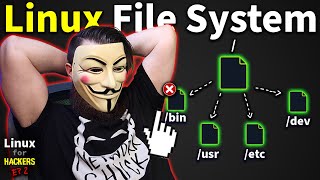
ls - Lists files and directories in your current location. Think of it as your digital map.
pwd - Prints the working directory, showing your current location in the file system.
cd - Changes the current directory, letting you move through the file system.
mkdir - Creates a new directory.
rm - Deletes files or directories. Be cautious—this is irreversible without backups.
cp - Copies files or directories to a specified location.
mv - Moves or renames files or directories.
touch - Creates an empty file.
File Reading and Text Processing Commands
cat - Displays the contents of a file.
less - Views a file one page at a time.
head - Shows the first few lines of a file.
tail - Displays the last few lines of a file, often used for logs.
echo - Outputs text to the terminal or writes text to a file.
grep - Searches files for a specific string or pattern.
awk - Processes and extracts fields from structured text files.
sed - Edits text streams or files using patterns.
tr - Translates or deletes characters in text streams.
cut - Extracts specific sections of text by columns or fields.
System and User Management Commands
whoami - Shows the current user’s username.
id - Displays user and group IDs.
adduser - Adds a new user with a home directory and configuration.
useradd - Creates a new user without a home directory by default.
usermod - Modifies a user account’s properties.
passwd - Sets or updates a user’s password.
deluser - Removes a user from the system.
chown - Changes the ownership of a file or directory.
chmod - Adjusts permissions on files or directories.
umask - Sets default permissions for new files and directories.
System Monitoring and Automation Commands
lsblk - Lists information about block devices, such as hard drives.
blkid - Displays unique IDs of block devices.
mount - Attaches a file system or storage device.
umount - Detaches a file system or storage device.
cron - Schedules repetitive tasks.
at - Schedules one-time tasks.
watch - Executes a command repeatedly, showing updated results.
sleep - Pauses execution for a specified duration.
Networking and Connectivity Commands
ping - Tests network connectivity by sending packets to a host.
traceroute - Maps the route packets take to a destination.
ifconfig - Displays or configures network interfaces.
ip - Manages IP addresses and routes.
nmap - Scans networks to find devices, open ports, and running services.
tcpdump - Captures and analyzes network packets.
curl - Transfers data to or from a server using various protocols.
netstat - Displays network connections and statistics.
Exploitation and Vulnerability Analysis Commands
sqlmap - Automates testing for SQL injection vulnerabilities in databases.
hashcat - Cracks hashed passwords using brute force or dictionary attacks.
metasploit - A framework for developing and executing exploits against systems.
burpsuite - Tests and identifies vulnerabilities in web applications.
dirb - Discovers hidden directories and files on web servers.
#hacking #commands