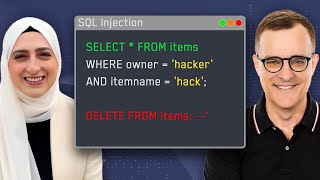
How to Hack Any Database using SQL Injection in Kali Linux?
💉 Welcome to Tech Sky's SQL Injection series! In this eye-opening tutorial, we're exposing how attackers can exploit vulnerable websites to access entire databases with just a few keystrokes. Join us as we uncover the techniques behind SQL injection and learn crucial protection strategies.
⚠️ *IMPORTANT DISCLAIMER:*
This tutorial is strictly for educational purposes and security research. The techniques shown should only be used in authorized testing environments. Unauthorized use of these methods is illegal and unethical. All demonstrations are performed in controlled lab environments using dedicated testing devices.
📚 *What You'll Discover:*
1. *00:00 - What Makes SQL Injection So Devastating?*
- The shocking prevalence of vulnerable websites
- Understanding the scope of database exploitation
- Real-world implications of SQL injection attacks
2. *02:14 - What is SQL Injection?*
- Understanding Structured Query Language fundamentals
- How SQL queries interact with databases
- Types of SQL injection vulnerabilities
3. *03:24 - How to Set Up a Testing Environment?*
- Installing and configuring DVWA
- Setting up Docker for secure testing
- Creating an isolated vulnerable environment
4. *07:21 - How to Perform Basic SQL Injection Attacks?*
- Understanding entry points for injection
- Simple query manipulation techniques
- Extracting multiple database records
5. *09:31 - How to Extract Sensitive Data Using UNION Attacks?*
- Determining database column structure
- Using UNION SELECT statements effectively
- Accessing usernames and passwords
6. *11:31 - How to Protect Against SQL Injection?*
- Essential developer security practices
- Parameterized queries implementation
- User-level protection strategies
7. *13:08 - Why is SQL Injection Still So Common?*
- The simplicity of exploitation
- Common security oversights
- The importance of secure coding practices
🚀 *Why This Matters:*
- Learn critical web security concepts
- Understand database vulnerability implications
- Master essential protection strategies
🔗 *Stay Tuned for More on Tech Sky:*
- Subscribe for future tutorials on cybersecurity and ethical hacking
(https://youtu.be/F-jXAWZHIrI)
(https://youtu.be/QGjrU2uqTbU)
(https://youtu.be/rUA9fXFyfLA)
📌 *Connect with Tech Sky:*
- Follow us on Instagram: (https://www.instagram.com/techsky.ig)
#TechSky #SQLInjection #WebSecurity #EthicalHacking #Cybersecurity #DatabaseSecurity #PenetrationTesting #LearnWithUs